
Injecting side effects by abusing comma operator
in C and C plus plus, programming / with 2 comments /
![]()
Comma operator can be used sometimes to inject side effects into expressions:
#include <stdio.h>
#include <stdlib.h>
#include <math.h>
int main() {
int max = 10;
double x = 0;
while (max--, printf("%d\n", max), max) {
/* sth */
}
x = printf("x: %f", x), x = sqrt(x), printf(", sqrt(x): %f\n", x), x;
return EXIT_SUCCESS;
}
Milionerzy: najlepsza kolejność wykorzystania kół ratunkowych
in programming / with No comments /
![]()
Grasz w milionerów, masz wszystkie koła ratunkowe i nagle dostajesz makabryczne pytanie. Nie wiesz. Bierzesz koła. Najpierw 50:50, a później publiczność, czy najpierw publiczność, a potem 50:50? Ta dyskusja rozgorzała na joemosterze, wiec i ja postanowiłem się temu przyjrzeć.
Warunki początkowe
Zakładam, że 10% osób zna odpowiedz na pytanie, a reszta zaznacza losową odpowiedz. Publiczność to około kilkadziesiąt osób, jest ich więc na tyle dużo, że można założyć, że odpowiedzi tych którzy strzelają rozłożą się równomiernie. Mamy zatem:
10% - osoby znające odpowiedz 90% - osoby zgadujące
Wariant I, najpierw 50:50
Jeśli weźniemy najpierw 50:50, to zostawimy publiczności wybór między dwiema opcjami, rozkład odpowiedzi będzie wyglądał następująco:
odpowiedz poprawna: 0.5 * 90% + 10% = 55% odpowiedz błędna: 0.5 * 90% = 45%
Poprawną odpowiedz wskaże 55% głosujących.
Różdżka, jak ją wykonać i jak się nią posługiwać?
in parapsychology / with 29 comments /
![]()
Zasada działania i wykorzystanie różdżek
Różdżki są od wieków wykorzystywane do poszukiwania żył wodnych, które mogą źle wpływać na samopoczucie lub do poszukiwania wody podczas kopania studni. Niektórzy próbują wykorzystywać je również do poszukiwania zaginionych przedmiotów, lub do przepowiadania przyszłości, zastosowania te zostaną również omówione w dalszej części artykułu.
Jak w przypadku każdej koncepcji nie do końca akceptowanej przez tradycyjną naukę, opinie, czy różdżka to użyteczny przedmiot czy bujda są podzielone. Sądzę, że różdżki działają, w ten sposób, że osoba która się nimi posługuje podświadomie wychyla dłońmi tak, by uzyskany wynik był zgodny z prawdą. Skąd osoba wie, jaki powinien być wynik? To już inna historia.
Zazwyczaj różdżki są wykonane albo z drutu, albo z gałązek, dziś skupimy się na tym, jak zbudować różdżkę tego pierwszego typu.

Osobiście skłaniam się ku teorii, że ruch różdżki spowodowany jest nieświadomym ruchem dłoni badającego. Skąd bierze się zatem ten ruch, i dlaczego jego efektem jest udzielenie poprawnej odpowiedzi? Jedna z koncepcji zakłada, że podświadomość stara się nam odpowiedzieć na pytanie, które postawiliśmy. Nasza podświadomość jest zaś częścią globalnej "podświadomości" i z niej czerpie potrzebne informacje.
How to hide an image inside another image?
in image processing, programming, Python / with 14 comments /
![]()
At first glance, there's nothing special on below image..

..but in fact, on this picture is hidden another one:

It was done, by using steganography, the second image was stored on two lowest bits of the pixels. On two bits we may save values from 0 to 7, pixel in the image may have values from 0 to 255, so such small change is not visible to the human eye.
Zipf's law and natural languages
in C and C plus plus, programming, R / with No comments /
![]()
If we count the appearance of words in a sample of (most) human languages, it's visible that they have the Zipf's distribution. It can be used to distinguish human languages (and humans) from texts generated randomly (by spambots). This is presented on below histogram:

Below I will present tools that I made to verify this, first of them is a C++ program used to parse a text and generate a distribution of words that he encountered, second is a R script used to generate diagram from mentioned distribution.
How to distinguish human languages by letter frequency histogram?
in C and C plus plus, programming / with No comments /
![]()
How to find without dictionaries a language of a text sample? It can be accomplished by comparing frequencies of letters in a sample and in known languages. For example in polish 'a' letter is about 0.0551146 of all letters, in french it's 0.049458 and in german 0.0434701.
I created a small program in C++ that takes as an argument path to file with unknown language and print, how this language differs from languages that he knowns. The lowest result is the best match. Frequencies of letters in known languages are computed from files in samples directory.
Below is the output for checked sample and this sample (in French):
bash-3.2$ ./a.out test3.txt difference between Polish language: 0.0965482 difference between French language: 0.0442431 difference between German language: 0.0945827
A simple trick to avoid "goto" statement
in C and C plus plus, programming, smart code / with 2 comments /
![]()
Error handling in C is sometimes done by using goto and labels. One of examples in the Linux kernel:
static struct avc_node *avc_alloc_node(void)
{
struct avc_node *node;
node = kmem_cache_zalloc(avc_node_cachep, GFP_ATOMIC);
if (!node)
goto out;
INIT_RCU_HEAD(&node->rhead);
INIT_HLIST_NODE(&node->list);
avc_cache_stats_incr(allocations);
if (atomic_inc_return(&avc_cache.active_nodes) > avc_cache_threshold)
avc_reclaim_node();
out:
return node;
}
There's a trick with the usage of do/while construction that allows to write the same without using goto label. The idea is presented on below:
// with goto label
if (!bar()) {
goto error;
}
someValue = baz();
error:
// with do/while construction
do {
if (!bar()) {
break;
}
someValue = baz();
} while (0);Przepis na kurczaka po chińsku
in life / with 2 comments /
![]()
Czas przygotowania: 30-40min, ilość porcji: 1-2 osoby.
Składniki
- 2 torebki ryżu
- 1-1.5 piersi z kurczaka lub indyka
- 0.5 opakowania chińskiej mieszanki warzyw
- 2-3 łyżki oliwy z oliwek
- 1 łyżka curry
- 2-3 łyżki sosu sojowego

Easier error handling by using automatic code generation [Perl interpreter]
in C and C plus plus, Perl, programming / with 2 comments /
![]()
Perl interpreter has an interesting mechanism to checks if function arguments have correct values. Below is its example from util.c:
char *
Perl_delimcpy(register char *to,
register const char *toend,
register const char *from,
register const char *fromend,
register int delim, I32 *retlen)
{
register I32 tolen;
PERL_ARGS_ASSERT_DELIMCPY;
/* ... */
}
Body of PERL_ARGS_ASSERT_DELIMCPY is in proto.h:
#define PERL_ARGS_ASSERT_DELIMCPY \
assert(to); assert(toend); assert(from); assert(fromend); assert(retlen)
What makes those macros interesting, is that they are automatically generated by a perl script (regen.pl). They are created from a data stored in embed.fnc, a sample entry of this file is presented below:
: Used in util.cp op |void |example_function |NN const char *name|STRLEN len|
The script needs to be executed after any change in embed.fnc.
Interesting and weird.
Remote control of devices by using PC Speaker
in C and C plus plus, electronic engineering, programming / with 2 comments /
![]()
This is one of my older projects that aims to control external devices directly, by using the PC Speaker port. It can control multiple devices at one go, but they must be powered one at a time. I made it a couple of years ago and it was working fine, but due to mistake during plugging it literally burned ;(
Now, when both cheap USB chips are available and PC speaker is unused (or integrated with sound card) it doesn't make sense, to build it, but this is still an interesting concept.
CMS written entirely in PL/pgSQL
in programming / with 1 comment /
![]()
In one of my previous jobs, I heard that it would be inspiring, to write a CMS with all logic stored and executed on database side. Every request would be performed in stored procedures, theirs final result would be HTML page sent back to the user.
I will present, how to do it with PotgreSQL, Apache, Linux and a bit of bash scripting. The script is a cheat because I promised to write everything in stored procedures, but as you will see, it's just a gateway to the database, there isn't any logic.
Version numbers can be tricky!
in programming / with 1 comment /
![]()
1.0 1.1 ... 1.8 1.9 1.10 1.11 ... 1.19 1.20 ...
Czym jest medytacja? Jak medytować? Popularne techniki medytacji.
in life, parapsychology / with 1 comment /
![]()
W codziennym życiu koncentrujemy się na otaczającym nas świecie, gdy jesteśmy w pracy zajmujemy sie pracą, gdy jedziemy autobusem patrzymy na świat za oknem, a gdy rozmawiamy z kimś, to słuchamy go i współuczestniczymy w rozmowie. To normalne zachowanie, dzięki któremu możemy utrzymywać się materialnie, istnieć w społeczeństwie czy też trafić po pracy do domu. Problem zaczyna się, gdy zewnętrznych spraw jest za dużo lub gdy boimy się pomyśleć o sobie.
Gdy brakuje czasu by zastanowić sie nad sobą, by dać sobie chwile wytchnienia, życie często staje się cięższe, co zaś prowadzi do tego, że jest gorzej i tym bardziej nie ma się czasu albo chęci by się nad sobą zastanowić. Błędne koło zamyka się, a efektem jest często rezygnacja, rozgoryczenie, lęki i depresje. Czytelnik na pewno spotkał się z ludźmi wiecznie narzekającymi na świat, na sprawiedliwość i wszytko na co się da narzekać.
How to use finite state machine in parsing of assembly language?
in programming, Python / with No comments /
![]()
Finite State Machine - abstract
Often data must be analyzed chunk by chunk, checked if all of those chunks are valid (if the chunk is valid itself and if it's valid in context of previous chunks) and when some actions must be taken according to each type of this chunks. This can be easily modeled using finite-state machines (FSM).
State Machine has its state and transitions. There is at least one entry state, there may be termination state.
One task can be done by using different FSMs, but of course we should create them as simple as possible. What is nice in those tools, is that they may be easily extended. You may add new states, transitions, split existing state into new ones or nest new FSM into existing state.
Title of this post may confusing to people looking for concepts to build their own compilers or parsers. Shortly, reading them requires parsing code on three levels: lexical, syntactical and semantical, but presented FSMs may be directly applied only in the first case.
In next posts we will explain in details this assembly language and show, how to made its virtual machine, where FSM will be used as a part of it.
How does recursive packing of a file changes its size?
in programming, R, riddle / with 1 comment /
![]()
How the size of a packed file will change if you will pack it again? How will it change if you do that again and again? Will it be the same, bigger of smaller? I checked this with popular kinds of files and below I will show the results. I used Bash script and R language to check this. Charts shows how the file size changes in each iteration, first bar is the size of original, unpacked file.

How to use regular diode as a photo-element?
in electronic engineering / with 3 comments /
![]()
There are special diodes, transistors and resistors designed to measure light intensity, sometimes even a regular LED is also used for this task, can be used. I was wondering, if any diode (in a package that doesn't block light rays) could be used? Today I will share the results of my experiments.
How to clean silver by using aluminum foil and salt water?
in chemistry / with 3 comments /
![]()
Silver may be cleaned in a simple way, all we need is a couple of materials that are present in every house. Today I will present this simple cleaning method.

- Use dish washing liquid and toothbrush to clean jewelry from dirt.
- Dissolve a spoon of kitchen salt into a glass of hot water.
- Put aluminum foil into the water, on the top of it put your silver jewelry.
- Wait 30 minutes, clean silver under current water and let it dry.
Mistakes during checking if a returned value is null
in C and C plus plus, crappy code, programming / with No comments /
![]()
This is a bit modified real word example, found by tool for static analysis. In this code, foo() is a function that returns pointer to std::string or null pointer.
std::cout << foo()->length() << std::endl;
There's obvious bug here: executing length() method on value returned by foo() without checking if this variable is not null. At first it looks that it could be fixed in below way:
if (foo()) {
std::cout << foo()->length() << std::endl;
}
Unfortunately above code is also invalid because it can't be sure that if a function once returned not null value, then it will returns it next time. This may be fixed in below way, where temporary variable was used to check if length() may be executed on variable retured by foo().
std::string* fooObj = foo();
if (fooObj) {
std::cout << fooObj->length() << std::endl;
}Homemade pressure sensor
in electronic engineering / with 8 comments /
![]()
Pressure sensor is an element that changes its parameters according to changes of pressure that is put on it. Today I will present how to build it by using common and cheap materials like chewing gum and pencil.

Constructing a homemade microphone
in electronic engineering / with 36 comments /
![]()
To create a simple homemade microphone you need only a bunch of common electronic elements and a solder. Today I will present, how this microphone can be built at home.

How to sort numbers from STDIN
in programming, riddle / with 5 comments /
![]()
You get 10 numbers on STDIN, each followed by newline character, after that you have to display those numbers sorted from the smaller to the bigger. You cannot use sorting algorithms.
The riddle of the stolen wood
Sometimes piles of wood are marked by paint to protect them against thiefs. Continuous line is painted on the trees that are on the top of the pile, if one will steal some of them, then painted line on remaining stack will be discontinuous. To illustrate this tactic I made below picture:

If a thief would like to hide his crime, then what should he do? Present an algorithm to take n% of original trees and leave continuous red line on the remain pile.
3 x if
in C and C plus plus, programming, riddle / with 3 comments /
![]()
Below snippets in C check if foo() and bar() returns nonzero value and execute something() if needed. Are they equivalent? Why?
// first version
if (foo() && bar()) {
something();
}
// second version
if (bar() && foo()) {
something();
}
// third version
if (foo()) {
if (bar()) {
something();
}
}Galvanic copper plating
in chemistry / with No comments /
![]()
Abstract
Galvanization is a method of coating metal objects with layer of other metal. It can be useful to protect against corrosion or to create decorative shapes on metal objects. Chemical background of this process is difficult, but the idea is simple (forgive me my indolence) - use electricity to move a bit of metal to the coated object.

This experiment should be done with carefully and away from fire! Explosive mixture of H2 and O2 is being created during this process.
Tools and materials
- plastic plate,
- one glass of warm water,
- pinch of kitchen salt,
- copper wire with removed isolation,
- aluminum tea-spoon,
- DC power supply (3-10V).
try/catch in C [PHP interpreter]
in C and C plus plus, PHP, programming / with 3 comments /
![]()
Abstract
PHP interpreter is written in C, but uses try/catch construct known from other popular languages. This approach is different from everyday C-like error handling, where it's done by using function return value or by modifying error variable passed as an argument to a function.
zend_try {
PG(during_request_startup) = 1;
php_output_activate(TSRMLS_C);
/* unimportant stuff */
} zend_catch {
retval = FAILURE;
} zend_end_try();
If one of instructions in a "try" block raises an exception then the evaluation of this block is terminated and execution flow moves to a "catch" block.
Weird casting in C++
in C and C plus plus, crappy code / with No comments /
![]()
What is the value of foo variable after execution of below line if foo is type of int?
foo = static_cast<int>(foo + 0.5);
Geek pendrive hidden in electrolytic capacitor
in electronic engineering / with No comments /
![]()
Intro
Usually pendrives have the same, boring design, I wanted to change it, so I made my own geeky pendrive. Now it's hidden in old electrolytic capacitor.


Access to object's fields by using pointer arithmetic
in C and C plus plus, crappy code, programming / with 2 comments /
![]()
Normally a method uses its object's field by using their name. It's presented below, where we want to get value of description field from getDescription method.
class Car {
std::string getDescription() {
return description; // <- we return value of this field
}
std::string description;
};
The same result can be obtained by using a bit of magic with this, pointers and casting:
#include <iostream>
class Car {
public:
Car (int _weight, int _maxSpeed, std::string _description) :
weight(_weight), maxSpeed(_maxSpeed), description(_description) {
}
std::string getDescription() {
return description;
}
std::string getDescriptionUsingThisKeyword() {
return *((std::string*)((int*)this + 2));
}
private:
int weight, maxSpeed;
std::string description;
};
int main() {
Car myCar(200, 200, "my best car ever");
std::cout << myCar.getDescription() << std::endl;
std::cout << myCar.getDescriptionUsingThisKeyword() << std::endl;
}
Output:
bash-3.2$ ./a.out my best car ever my best car ever
It's error-prone, e.g. when someone changes order of fields in the class. I think, that it's cool but I wouldn't like to see this in a real code :)
Images hardcoded in a source code [PHP interpreter]
in C and C plus plus, image processing, PHP, programming, smart code / with 1 comment /
![]()
Abstract
Recently I presented a simple way to protect an image against saving, today I will show how PHP interpreter protect some of its images against changing.
Image may be hardcoded in a regular array, where each field contains corresponding value of a byte in the original image file. You may imagine that you open image in a hex editor, you see its content as a chain of values of the bytes, and then you retype them as a fields in your array (this can be automatized of course).
Smarter strings in C
in C and C plus plus, programming, smart code / with No comments /
![]()
In C, strings are usually stored in variables with char* type, it's just container for characters, there isn't stored other data/metadata. This can be tedious, e.g. if we want to iterate thought string we need to obtain its length (e.g by invoke strlen() function on it) or carry its length in some additional variables.
This can be simplified by wrapping raw char* string in a simple structure. Its string's length has unsigned type, therefore mistakes with assigning negative values will be easier to find. Its first argument is its content (with char* type), so it can be just passed to functions, that requires regular char* arguments (although it will create warning, it's safe IMHO).
Here is implementation:#include <stdio.h>
#include <string.h>
typedef struct string {
char* data;
unsigned length;
} string;
int main() {
string myHome;
myHome.data = "it's big and white";
myHome.length = strlen(myHome.data);
// now we don't have to check for size of string,
// e.g. we don't have to use strlen() to iterate thought charcters
int i;
for (i = 0; i < myHome.length; i++) {
printf("%c", myHome.data[i]);
}
printf("\n");
// backward compatibility with char*
printf("%s\n", myHome.data);
printf("%s\n", myHome); // this will raise warning but is legal
}
It's a bit unpopular trick, but may be seen in snippets on some forums, also here is tutorial about similar implementation of such strings.
How to replace modulo operator by using bitwise AND operator?
in C and C plus plus, programming, Python, smart code / with 11 comments /
![]()
Modulo operation on a and b returns a reminder from dividing a by b. It can be implemented by using bitwise AND operator if b is a power of two.
Following samples in C and Python illustrate it.
#include <stdio.h>
int main() {
// 8(dec) = 1000(bin)
// 7(dec) = 111(bin)
printf("19 mod 8 (with %%) %d\n", 19 % 8);
printf("19 mod 8 (with &) %d\n", 19 & 7);
// 16(dec) = 10000(bin)
// 15(dec) = 1111(bin)
printf("16 mod 16 (with %%) %d\n", 16 % 16);
printf("16 mod 16 (with &) %d\n", 16 & 15);
}
bash-3.2$ llvm-gcc modulo.c && ./a.out 19 mod 8 (with %) 3 19 mod 8 (with &) 3 16 mod 16 (with %) 0 16 mod 16 (with &) 0
bash-3.2$ python Python 2.6.1 (r261:67515, Feb 11 2010, 00:51:29) [GCC 4.2.1 (Apple Inc. build 5646)] on darwin Type "help", "copyright", "credits" or "license" for more information. >>> 19 % 8 3 >>> 19 & 7 3 >>>
Why do we need to decrease b?
Super-resolution algorithm in Python
in image processing, programming, Python / with 9 comments /
![]()
Abstract
Super-resolution algorithms is a family of algorithms used to obtain higher resolution image from set of images in lower resolutions. It's important to notice that by using those methods the higher resolution image is more detailed in opposition to resizing and debluring.
It may be applied on many different data, including spying and meteorological satellites, telescopes, tomographs and X-ray machines. Super-resolution algorithms can be also applied to 3D sceneries or sounds.
In this article, I will describe a super resolution algorithm proposed by Irani and Peleg and its simple implementation in Python.
One of low resolution images (for easier comparison it's resized to fit the estimated image):

The image estimated by using super resolution algorithm:

Renewable source of electricity from an old step motor
in electronic engineering, programming / with No comments /
![]()
Recently I saw in old electronic magazine reprint of a project, where step motor was used as a source of power for LED torch. It's an interesting idea of using renewable and simple source of energy. Today I will present my own construction. It can be used as a source of energy for devices like a wall clock or a single LED.
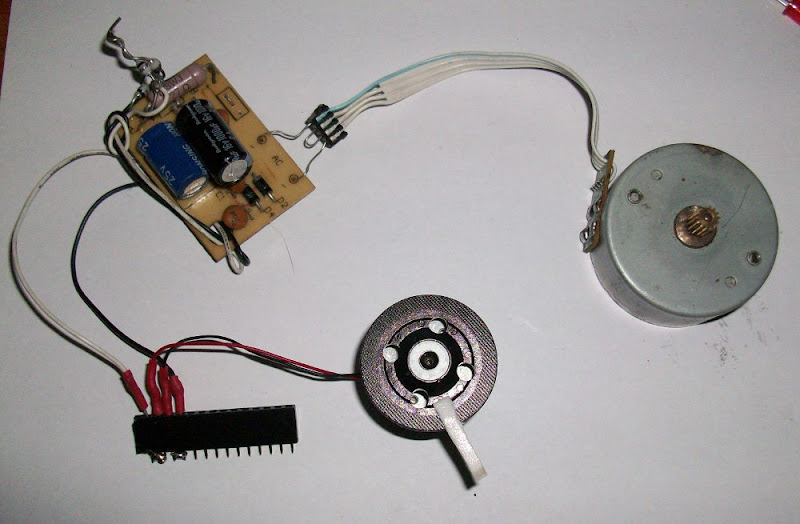
Constructing a homemade speaker
in electronic engineering / with 2 comments /
![]()
It's a simple speaker that can be built at home from inexpensive and freely available materials: magnet, cardboard and tape, isolated wire from signal transformer and mini-jack cable from broken headphones.
8 Best Programming Songs
in programming / with No comments /
![]()
Code monkey
Written by Jonathan Coulton, link to the lyric. I love this song, maybe because I'v worked a lot of time in different corporations :)
Kill dash nine!
There's a guitar player in the clip even when there isn't guitar part in the song :)
HOWTO avoid mistakes in conditional instructions
in C and C plus plus, programming, smart code / with No comments /
![]()
In C or C++ it's easy to made mistake in expression of conditional instruction and use assignment instead of comparison. It's presented in below snippet, where we want to check if x is equal to 6:
int main(){
int x;
/* first case */
/* OK */
if(x==6){
/* sth */
}
/* WRONG */
if(x=6){
/* sth */
}
/* second case */
/* OK */
if(x!=6){
/* sth */
}
/* WRONG */
if(x=!6){
/* sth */
}
return 0;
}
This code will be compiled successfully because its syntax is valid.
Those mistakes may be reduced by using following practice: while comparing something unmodifiable (string, number..) and variable, variable is written always on the right side. It's presented below:
int main(){
int x;
/* first case */
/* OK */
if(6==x){
/* sth */
}
/* WRONG */
if(6=x){
/* sth */
}
/* second case */
/* OK */
if(6!=x){
/* sth */
}
/* WRONG */
if(6=!x){
/* sth */
}
return 0;
}
Now conditional instructions with mistakes contain incorrect syntax and may be caught and fixed during compilation:
rgawron@foo:~$ gcc s2.c s2.c: In function ‘main’: s2.c:10: error: lvalue required as left operand of assignment s2.c:20: error: lvalue required as left operand of assignment
Protecting images against saving
in programming, Python / with No comments /
![]()
If you share on the Internet your images, then you may want to protect them against saving. There're a lot of ways to do it - watermarks, cutting images into multiple smaller pieces and reassembling them by using CSS, tricks with CSS or JavaScript and others. None of them is accurate against experienced user, but they are sufficient in most cases.
Today I will show different approach to protecting images, it's a bit impractical due to high CPU usage on browser side, but it works. The idea is to convert image into HTML table, where each pixel is one cell with corresponding to this pixel location and color.
Project contains three parts: Python script, HTML template and CSS file. The script requires as an argument location of the input image, as an output it generates output.html file. This file should be stored in the same directory as inline_image.css file. The sources are available on GitHub (image2table directory).
Making captcha easier to break
in image processing, programming, Python / with 12 comments /
![]()
Almost all sites use images with text that user has to retype to prove that he's a human not spambots. A lot of those images (called captcha) contains small lines, dots and other noises to make theirs analyze more difficult for spambots. In this post I will present how to easily remove this noise from a captcha.


I used Python and its PIL library for processing captchas. The first step is to transform image to grey-scale (this makes further work easier) and blur it (it makes small objects less visible). PIL's blur filter is a bit poor for that, but SMOTH filter works great (but it needs to be applied twice made it blurred enough). Next step is to check all pixels if their value is higher that some certain constant, if yes, then pixels will become white, if not they will be black. This constant may be set from command line.
Less popular way to copy content of a structure
in C and C plus plus, crappy code, programming / with No comments /
![]()
There is instance (let's call it p0) of structure, we create new instance (p1) of the same structure and want to copy content of fields from p0 to p1.
The simplest (IMHO also the best) way is to copy field by field. It's presented in following code (in case of p1 all fields are copied, in case of p2 only some).
/* output:
foo (3.800000, 4.900000): #121212
bar (3.800000, 4.900000): #335566
*/
#include <stdlib.h>
struct Point {
char desc[5];
double x, y;
char color[8];
};
int main() {
struct Point p0 = {.desc = "foo", .x = 3.8, .y = 4.9, .color = "#121212"};
struct Point p1;
snprintf(p1.desc, sizeof(p1.desc), p0.desc);
p1.x = p0.x;
p1.y = p0.y;
snprintf(p1.color, sizeof(p1.color), p0.color);
printf("%s (%f, %f): %s\n", p1.desc, p1.x, p1.y, p1.color);
struct Point p2;
snprintf(p2.desc, sizeof(p2.desc), "bar");
p2.x = p0.x;
p2.y = p0.y;
snprintf(p2.color, sizeof(p2.color), "#335566");
printf("%s (%f, %f): %s\n", p2.desc, p2.x, p2.y, p2.color);
return EXIT_SUCCESS;
}
The second way is use memcpy to copy content of memory allocated for p0 directly into p1. It's presented in next snippet.